- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
HTTP Strict Transport Security (HSTS) in Qlik Sense
Sep 9, 2022 3:51:29 AM
Feb 7, 2018 7:57:25 PM
HTTP Strict Transport Security (HSTS) is an opt-in security enhancement which any web application can support through the use of a special response header. When a supported browser receives this header that browser will prevent any communication sent over HTTP in the future and will redirect all traffic over HTTPS instead.
More details about HSTS can be found on https://cheatsheetseries.owasp.org/cheatsheets/HTTP_Strict_Transport_Security_Cheat_Sheet.html
Resolution
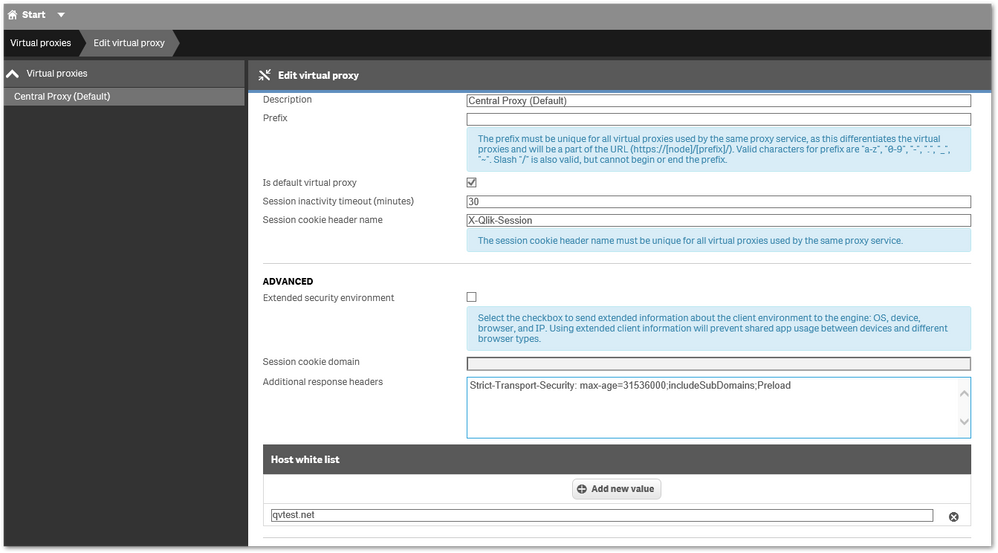
In Qlik Sense, one can add additional HTTP response headers in the Virtual Proxy configuration to enforce HSTS
- Open the Qlik Sense QMC
- In the CONFIGURATION SYSTEM section, click on Virtual Proxies
- Select the Virtual Proxy profile for user access and click on Edit
- Go to the Advanced section and in the field "Additional response headers"
- Enter the HSTS configuration setting applicable to your environment. i.e Strict-Transport-Security: max-age=31536000;includeSubDomains;Preload
- HTTP to HTTPS must be enabled.
For additional information about HTTP to HTTPS redirects, see
- How to: Redirect HTTP to HTTPS in Qlik Sense
- Qlik Community: Qlik Sense redirect HTTP to HTTPS
- and feature request Sense Initial URL redirect to /hub (http)
Sites to Confirm HSTS setup
- https://hstspreload.org/
- https://tools.geekflare.com/hsts-test
- https://dev.ssllabs.com/ssltest/
- https://nvisium.com/blog/2014/04/25/is-your-site-hsts-enabled.html
Gov Site on HSTS https://https.cio.gov/hsts/
Note: Qlik does NOT support the configuration or implementation of non-Qlik or Operating System related software. The above suggestion is an introduction to this topic, and if it does not work in your particular environment then please reach out internally to your IT team. If you need direct assistance, please contact your Account Owner to discuss purchasing Consulting Services. (see How to Contact the Consulting Team?)
Environment:
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
I understand that the above configuration is for connections via a proxy, and connections to ports like 4242 and 4239 should not be user-facing through a browser. Our client has identified a vulnerability indicating that the remote web server is not enforcing HSTS, as defined by RFC 6797, on ports 4242, 4239, and 4899. Is it possible to address this issue?
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hello @fabdulazeez
If you have identified a security concern, please report your concern as a support case as per Qlik Security Vulnerability Policy.
All the best,
Sonja
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Sorry for the incorrect word in the previous query. I meant that the client has shared a vulnerability, "HSTS Missing From HTTPS Server (RFC 6797)," for ports 4239, 4242, and 4899.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hello @fabdulazeez , I got the Same vulnerability raise from the Client side, do you have any workaround for this? Any Help from the Qlik Side on this?