- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Quick guide to configure IIS as a Reverse Proxy with HTTPS and Qlik Sense
May 11, 2021 7:07:39 AM
Dec 8, 2017 4:10:58 PM
Environment:
Qlik Sense Enterprise on Windows
This documentation is only for testing and use as a possible base for configuration. Anything not shown in the steps are considered default and no extra settings need to be applied/modified. Any issues with IIS or its configuration/use will need to be brought to the attention of Microsoft or the environments proper IT support team. Qlik does NOT support IIS nor its features/installation.
It is not guaranteed this will work in every environment, due to Corporate/IT policies. Use this information at your own discretion.
Environment:
- Central Node: qlikserver1.domainl.local
- IIS / Reverse Proxy: qlikserver2.domain.local
- Firewalls are OFF
- Single Domain
- Clean Environment and Open / Non-restrictive Group Policies
- OS: Windows 2012 R2, Windows 2016 Standard.
- Qlik Sense: November 2017, September 2020
! The information in this article is provided as-is and to be used at own discretion. Depending on tool(s) used, customization(s), and/or other factors ongoing support on the solution below may not be provided by Qlik Support.
Items Required:
- Valid and trusted 3rd party certificate chain for both the Qlik Sense Proxy server AND the IIS Reverse Proxy server
- These certificates must be exportable, have the Private Key and the full certificate chain (including the Trusted Root)
- These should be provided and installed prior to configuring the IIS Reverse Proxy
- They CAN be installed after, but for this documentation they should already be in the environment.
- Instructions on importing/installing the certificates for Qlik Sense and the IIS server are located at the end of the documentation (Installing a 3rd Party certificate with its Trusted Root)
- Example: TinyCerts.org – You can create your own CA and then certificates against that CA for any server name requested. Note: This option requires less steps but certificates issued via TinyCerts are not considered to be ready for production environments. Certificates issued by a Certificate Authority is recommended.
- NOTE: This test will NOT work if these are not provided and installed correctly
- IIS8 or later
- Due to WebSocket connections not being supported in earlier versions
- The Virtual proxy used for testing has the IIS machines Server Name / FQDN / IP / Alias / Vanity URL in the Host white list (Review Step 8-A below for more information).
- Windows Active Directory – Authentication
- The virtual proxy used for these instructions must be configured to use Windows authentication (not SAML/JWT/Forms/Header)
Steps
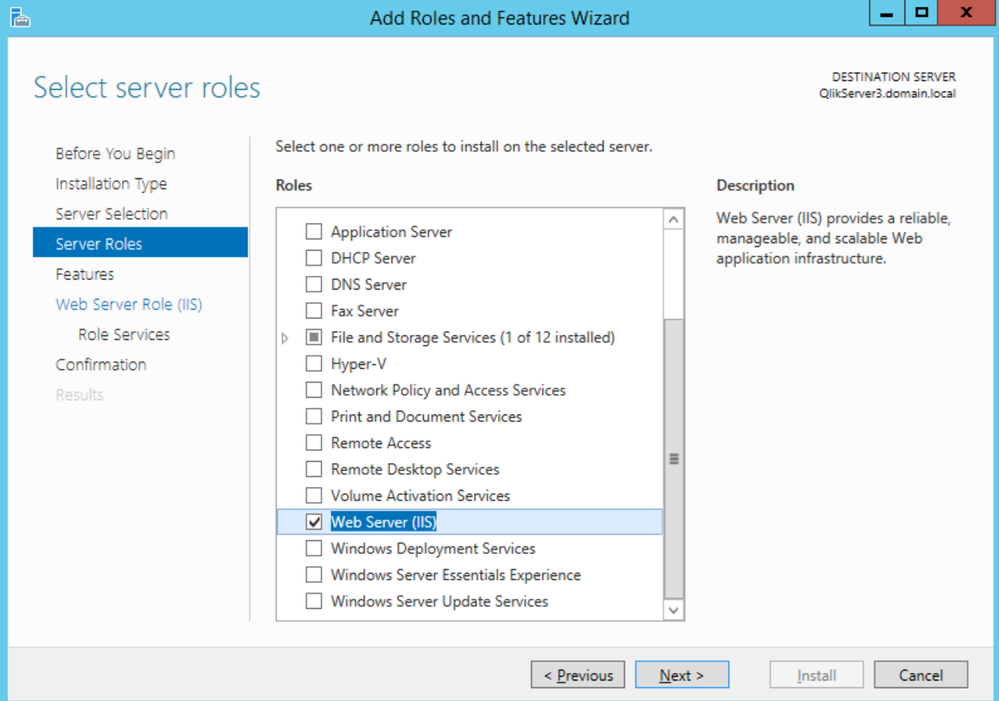
- On the Windows Server, go to Add Roles and Features
- Install the Server Roles - Web Server (IIS)
- Finish the installation.
- Download and install AAR from Application Request Routing v3. Older environments may need to follow the steps under http://blogs.technet.com/b/erezs_iis_blog/archive/2013/11/27/installing-arr-manually-without-webpi.a... The following components are installed:
- Web Farm Framework module (not needed by ARR v3, see Microsoft Application Request Routing 3.0 (x64))
- External cache module
- URL Rewrite Module
- ARR
NOTE: Links directly to these downloads will not be provided. The referenced blog provides them (as of 12/1/17) and were used in documentation. Microsoft Web Platform Installer (https://www.microsoft.com/web/downloads/platform.aspx) can be used to download the required components. Use your own discretion on how you download and install these IIS modules.
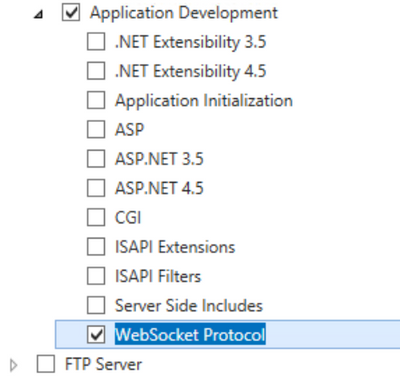
- Return to the Add Roles and Features and activate WebSocket Protocol
- Finish the Installation
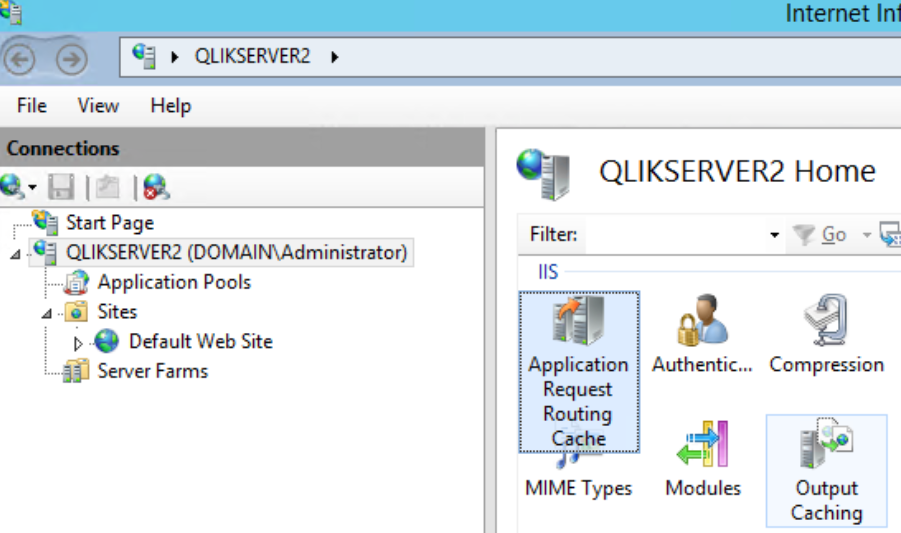
- Run the Information Services (IIS) Manager
- Click on the Server and select Application Request Routing Cache
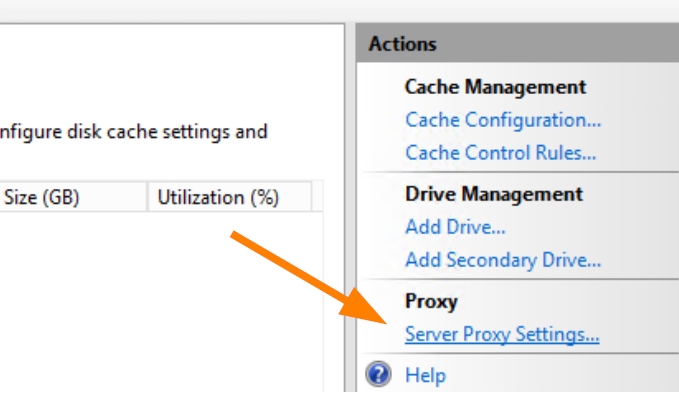
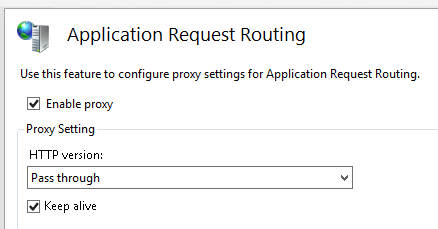
- Select Server Proxy Settings under Actions - Proxy on the right side Activate the proxy by checking the box “Enable proxy”
- Activate the proxy by checking the box “Enable proxy”
- Click on the Server and select Application Request Routing Cache
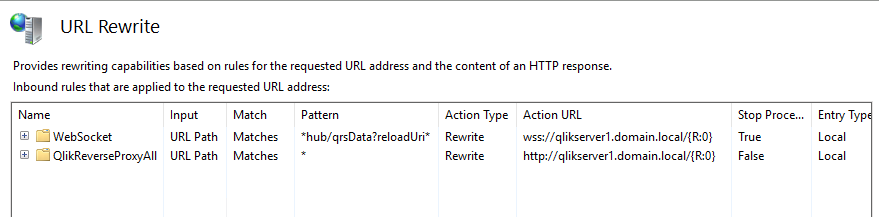
- Select the URL Rewrite under Actions – Advanced Routing
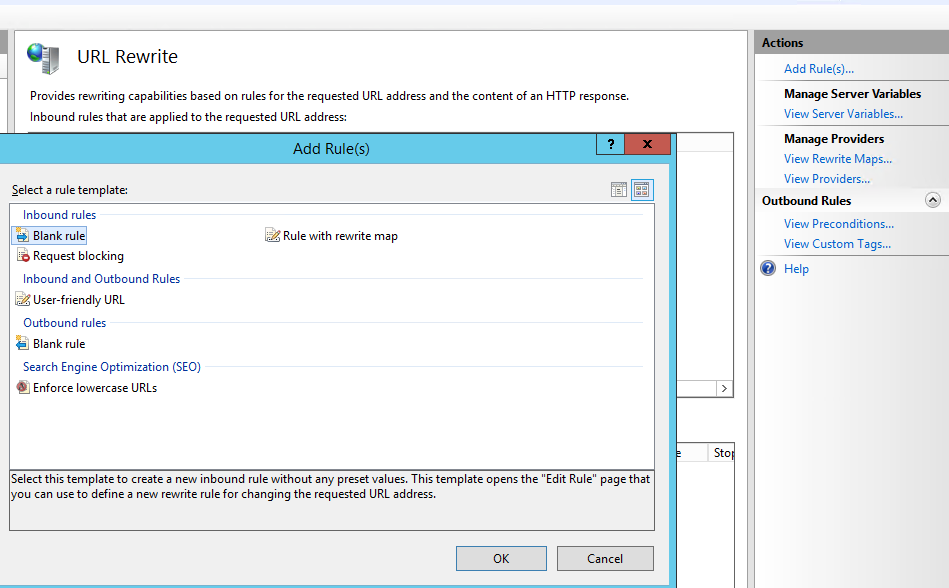
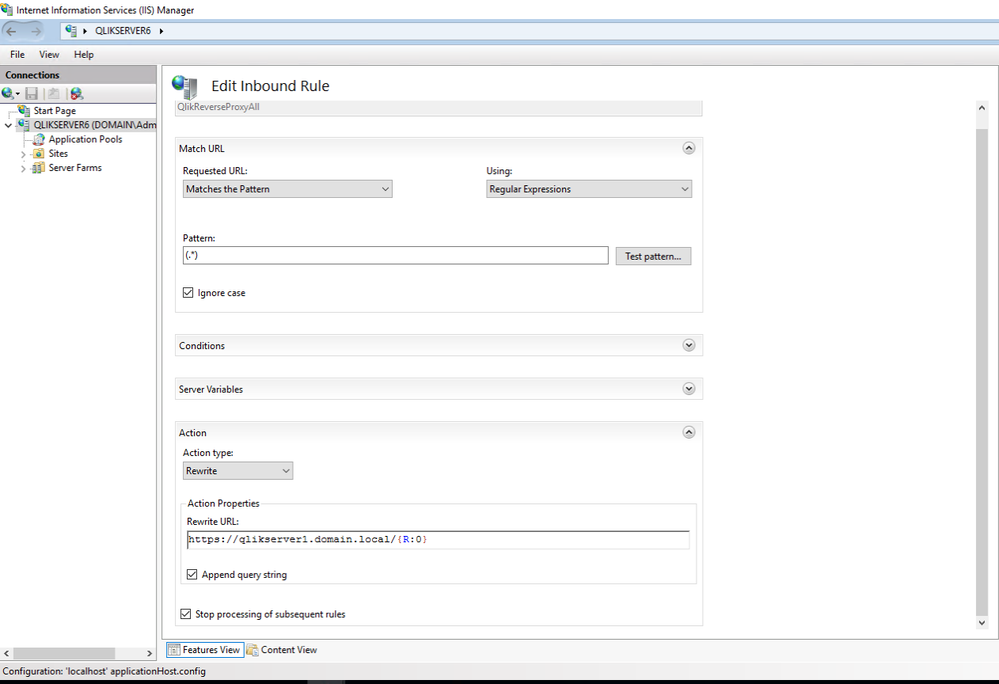
- Click Add Rule(s) under Actions and select a Blank rule template. Name it QlikReverseProxyAll.
-
Set https://qlikserver1.domain.local/{R:0} (NOTE: Use your own Qlik Sense Proxy URL) under Rewrite URL
-
Add (.*) under Pattern
-
Click on Apply under the Actions pane, then on Back to Rules.
-
- Click Add Rule(s) under Actions and select a Blank rule template. Name the rule "WebSocket". Note that this rule is specially needed on newer versions of Qlik Sense where Websocket is used by default, and required to gain Hub access. Note: This rule works so long as the Subject Alternative Name used for the certificate used in binding on step 5 below has the Qlik Sense server name, NOT the proxy server name. So the DNS record (in this example qlikserver1.domain.local) needs to be updated to have the appropriate IP mapping (IP of the proxy server). The system's hosts file may be manipulated for testing, instead.
-
Use Wildcards to match the pattern *hub/qrsData?reloadUri*
-
Rewrite URL: wss://qlikserver1.domain.local/{R:0}
-
Make sure to check Stop processing of subsequent rules
-
Click on Apply under the Actions pane, then on Back to Rules.
-
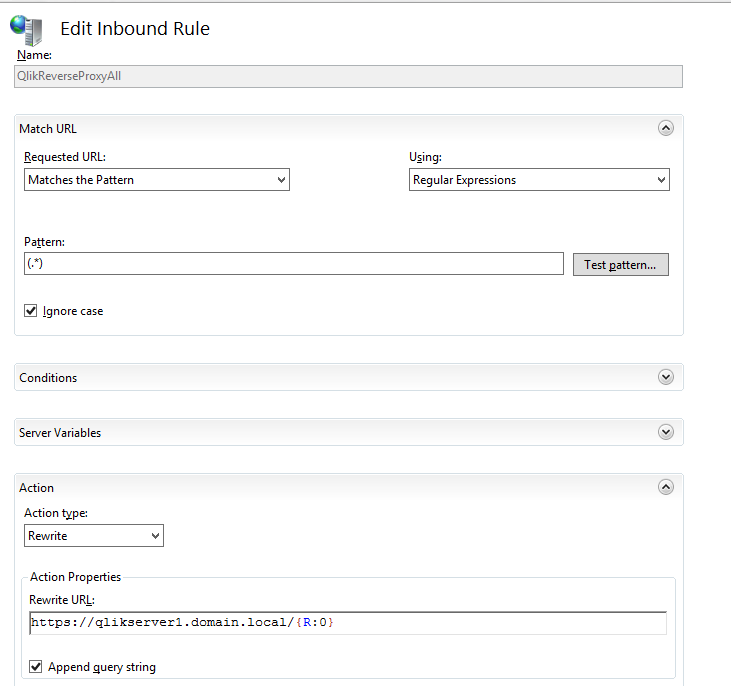
- Click Add Rule(s) under Actions and select a Blank rule template. Name the rule "AuthForwarding".
NOTE: As of Qlik Sense February 2018, the Port 4244 / AuthForwarding is NO longer needed for Windows Authentication and is NOT needed for any other authentication types (SAML / Header). This port has been made internal and doesn't need to be addressed by the Proxy.
-
Add “/windows_authentication/” under Pattern.
-
Set "https://qlikserver1.domain.local:4244/{R:0}" (NOTE: Use your own Qlik Sense Proxy URL) under Rewrite URL
-
Click on Apply under the Actions pane, then on Back to Rules.
-
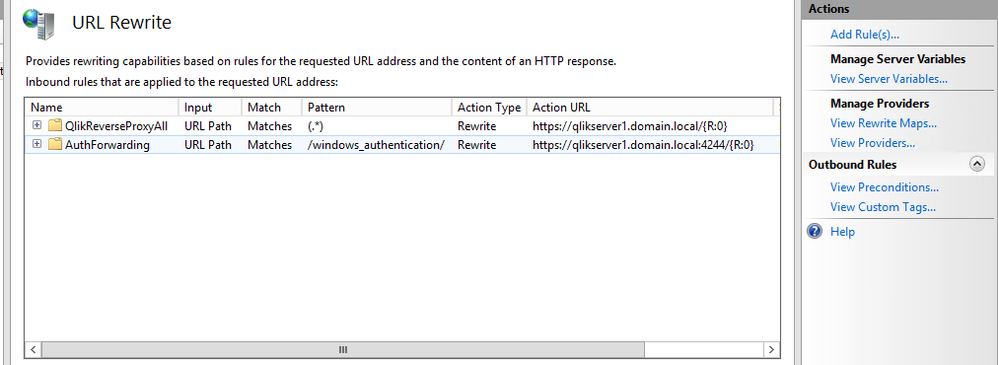
- URL Rewrite should have at least two entries for Qlik Sense. See scenarios below. For b, make sure WebSocket is moved to the top by selecting it and clicking on Move Up.
- Scenario on older versions of Qlik Sense:
- Scenario in newer versions of Qlik Sense:
- Scenario on older versions of Qlik Sense:
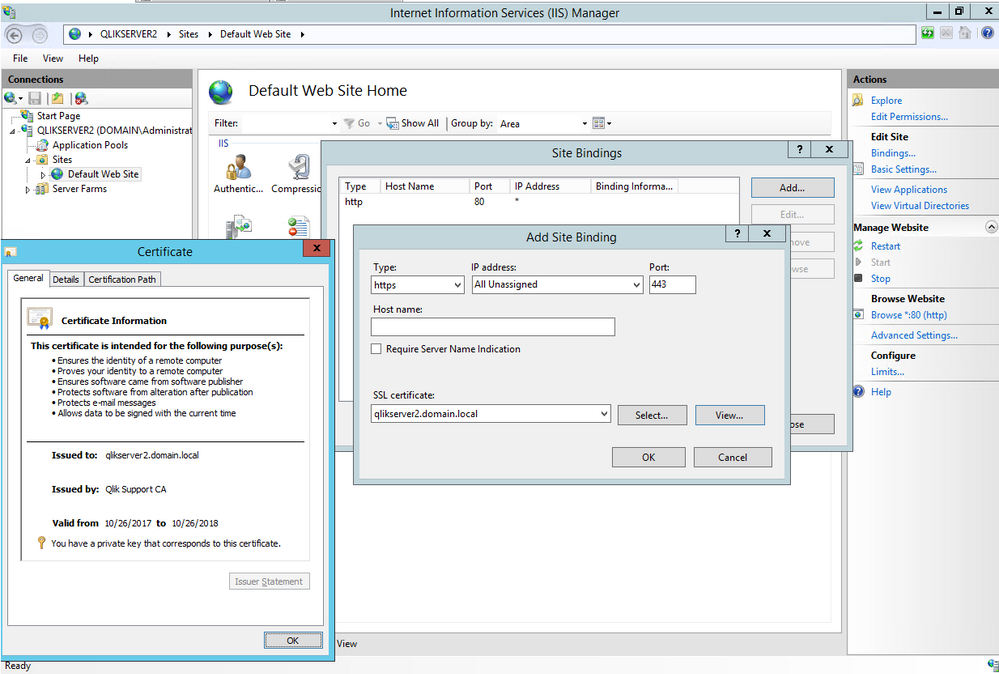
- Bind the valid and trusted 3rd Party Certificate to IIS for HTTPS AND Port 443 (NOTE: This is not a Qlik operation)
-
Verify that the Proxy server (qlikserver1.domain.local) has a certificate that trusts the certificate now bound and used by the IIS Reverse Proxy
NOTE: In this example we are using the same CA, with the same Trusted Root and the certificates are set for the two machines FQDN. This is not within Qlik control to give instructions on the exact setup and allowed actions within individual environments for this process. - Attempt and verify by logging into the Hub using the IIS server name
Updating Media
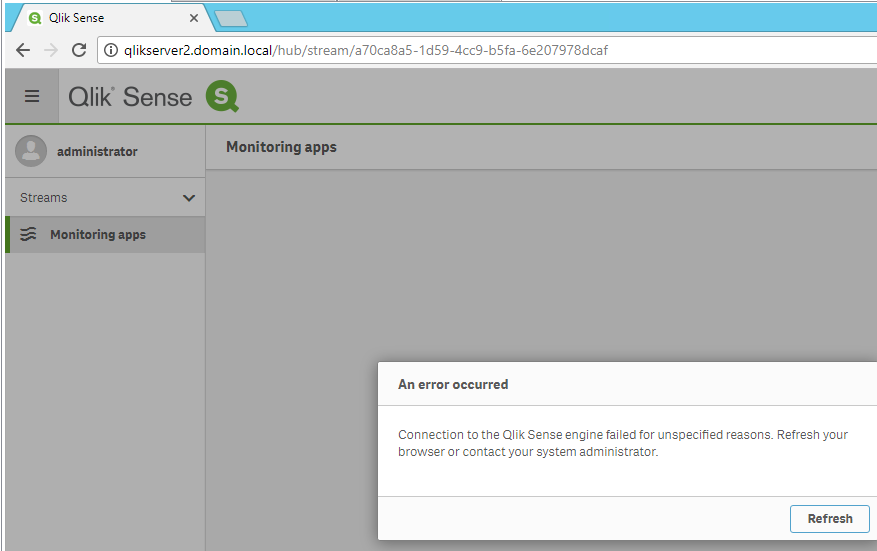
NOTE: If you did not add the IIS server (Name/FQDN/IP) to the Host white list for the Virtual Proxy that you’re connecting to, it will fail with a similar image. (Example shows HTTP, but the same will happen for HTTPS)-
You can mitigate this by adding the domain suffix.
In the example above you can see domain.local is added to fix the issue. This is because the URL does not originate from the Central, but from the IIS / Reverse Proxy server, so it doesn’t trust it. Adding the domain.local will trust any URL with domain.local in it. If you used an IP, it would fail as well due to this virtual proxy not trusting it. NOTE: Adding the server name/DNS Alias/IP/Vanity URL to this section should added when using Reverse Proxies as they will not be trusted by default.
-
Installing a 3rd Party certificate with its Trusted Root:
Install/import a valid certificate for the IIS Reverse Proxy server with a Trusted Root from a Certificate Authority. This will be used to make sure both the SSL certificate bound to the Qlik Sense Proxy and IIS to trust each other.
The images below are from a .PFX file that has both the Local Computer – Personal certificate for the FQDN of DC1.domain.local and the Trusted Root certificate. When imported or installed it will place both certificates in their proper locations.
NOTE: You may receive the certificate in a different format, please review with your CA / IT team to understand how to install and configure the certificates within your environments if these directions are not applicable
NOTE 2: The manual installation steps are below. These same steps can be used to import or install the certificate on both the Sense and IIS environments (this is not a Qlik specific operation).
https://help.qlik.com/en-US/sense/November2017/Subsystems/ManagementConsole/Content/change-to-signed... - States how to apply the new HTTPS/SSL thumbprint to the Proxy server on Qlik Sense.
Import the certificate
- Launch Microsoft Management Console (mmc.exe) on the Proxy node
- In the MMC, go to File > Add / Remove Snap-in...
- Select Certificates and click Add
- Select Computer account, click Next, select Local computer and click Finish
- In the MMC, go to Certificates (Local Computer)/Personal
- In the MMC, go to Actions > All Tasks > Import...
- Browse to the certificate file provided to you from your CA / Export from the QMC
- Follow the instructions on the screen to import the certificate, including the private key
- Verify the new certificate has been imported into Certificates (Local Computer) > Personal > Certificates and that it contains a private key
- Viewing the certificate when installed should have this entry:
- Follow the same steps to for the Trusted Root, but place it in Certificates (Local Computer) > Trusted Root Certification > Certificates
(More Generic information and steps: https://help.qlik.com/en-US/sense/November2017/Subsystems/ManagementConsole/Content/change-proxy-cer...)
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi @pbr , thank you for this great article !
in the prerequesites, you mentioned
- Windows Active Directory – Authentication
- The virtual proxy used for these instructions must be configured to use Windows authentication (not SAML/JWT/Forms/Header)
does it mean it is not possible to use this with SAML authentication ?
Best regards
Joh
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
@jchoucq This was configured for an older version of Qlik Sense where another Port was needed for Windows Authentication (4244). The documentation was originally created for that Auth Method and wouldn't work for others with that excerpt there to note the point.
However, since Sense no longer uses it, the instructions should work for most authentication methods when using Step 12-b, depending on different factors such as where and how the auth module is located and accessed.
I did a quick test using the above instructions on Feb 2021 of Qlik Sense and did not need the Websocket URL Rewrite entry. The only stipulation is I could not log into Windows Authentication while local to the the Qlik Sense server (QlikServer1.domain.local) and would loop the browser login dialog. However, External worked for both URLs: QlikServer6.domain.local and QlikSense.domain.local, including from DC1. QlikServer6 is where the below screenshot is from and is what is running IIS in this environment.
--
SAML: This will work for Windows and Header (depending on injection method) at least, but SAML will likely fail due to the Reverse Rewrite Response Header forcing the IdP Redirect URL to be masked as well.
IE: https://qliksense.domain.local/saml will attempt to call to https://qliksense.domain.local/adfs/ls/?SAMLRequest= which is incorrect as the actual IdP URL call would be https://dc1.domain.local/adfs/ls/?SAMLRequest= where the AD FS is installed.
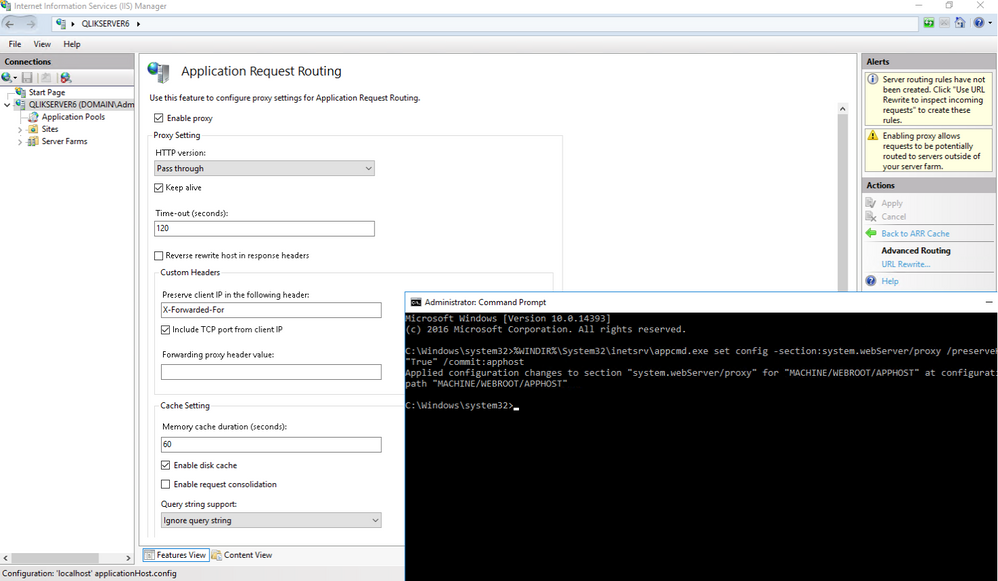
To fix this issue there's a few ways, but a simple one I found for testing is disabling the "Reverse rewrite host in response headers" under the Application Request Routing and performing:
- Run Command Prompt as Administrator
%WINDIR%\System32\inetsrv\appcmd.exe set config -section:system.webServer/proxy /preserveHostHeader:"True" /commit:apphost
https://serverfault.com/questions/874780/net-issue-on-adfs-sso-behind-a-reverse-proxy
Note: This worked local from QlikServer1 without any issue unlike Windows.
--
Depending on Security concerns and needs, there's other ways to perform this as noted through the Response Headers - https://steveoams.com/blog/qlik-sense-reverse-proxy-config-for-iis and documented methods through Microsoft - https://docs.microsoft.com/en-us/iis/extensions/url-rewrite-module/modifying-http-response-headers
Depending on the need, the Pattern could be different than (.*).
https://docs.microsoft.com/en-us/iis/extensions/url-rewrite-module/creating-rewrite-rules-for-the-ur...
https://nicolas.guelpa.me/blog/2015/02/21/rewrite-redirect-iis.html
https://www.yaplex.com/blog/examples-of-my-most-useful-iis-rewrite-rules
Note: "Stop processing of subsequent rules" may need to be checked or unchecked depending on other rules, but for testing purposes, either / or works if there's no others.
Hope this helps!
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
thanks a lot @pbr for all these details on this specific subject which is clearly not easy for me 😉
Thanks again !