Unlock a world of possibilities! Login now and discover the exclusive benefits awaiting you.
- Qlik Community
- :
- Support
- :
- Support
- :
- Knowledge
- :
- Support Articles
- :
- Qlik Sense: How to decrypt a SAML assertion or err...
Options
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Qlik Sense: How to decrypt a SAML assertion or error message
No ratings
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
Support
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Qlik Sense: How to decrypt a SAML assertion or error message
Last Update:
Jul 7, 2022 7:12:31 AM
Updated By:
Created date:
Oct 29, 2017 8:02:13 AM
How to decrypt a heavily encoded SAML message.
If you have set up the Identity Provider to encrypt the SAML assertion, then in order to see what it contains for troubleshooting, you will need to decrypt it.
Environment:
Qlik Sense Enterprise on Windows , all versions
It is important to understand the 3 below concepts when using SAML.
- Inflation and base-64 encoding
- Signing
- Encryption
A SAML AuthnRequest is:
- Inflated and base-64 encoded (If you use a SAML browser extension, it will deflate it and decode it automatically for you. In order to do that manually, https://www.samltool.com/decode.php can be used.)
No private key is needed to deflate/decode. - Signed, so that it cannot be altered. The signature does not hold any useful information for troubleshooting, it is just to make sure that the SAML request hasn't been altered. However if the certificate it has been signed with does not correspond, you won't be able to authenticate.
The Qlik Sense certificate is needed to validate the signature on the SAML assertion. (Note: Qlik Sense always signs SAML AuthnRequest, this cannot be disabled, however SAML AuthnRequest signature validation can be disabled in the Identity Provider)
A SAML assertion (The assertion is a section in the SAML response) is:
- Inflated and base-64 encoded (If you use a SAML browser extension, it will deflate it and decode it automatically for you. In order to do that manually, https://www.samltool.com/decode.php can be used.)
No private key is needed to deflate/decode. - Signed, so that it cannot be altered. The signature does not hold any useful information for troubleshooting, it is just to make sure that the SAML request hasn't been altered. However if the certificate it has been signed with does not correspond, you won't be able to authenticate.
The Identity Provider certificate is needed to validate the signature on the SAML assertion. - Encrypted (Optionally). In this case, in order to see if information in the SAML assertion are correct, decrypting the SAML assertion is needed.
It can be decrypted with https://www.samltool.com/decrypt.php, just paste the deflated/decoded SAML request.
The Qlik Sense certificate private key is needed to see what the signature holds.
The SAML response is generated by the Identity Provider and the public certificate of the Service Provider (Qlik Sense) is used to encrypt. You will need the private key of Qlik Sense to decrypt it.
Resolution:
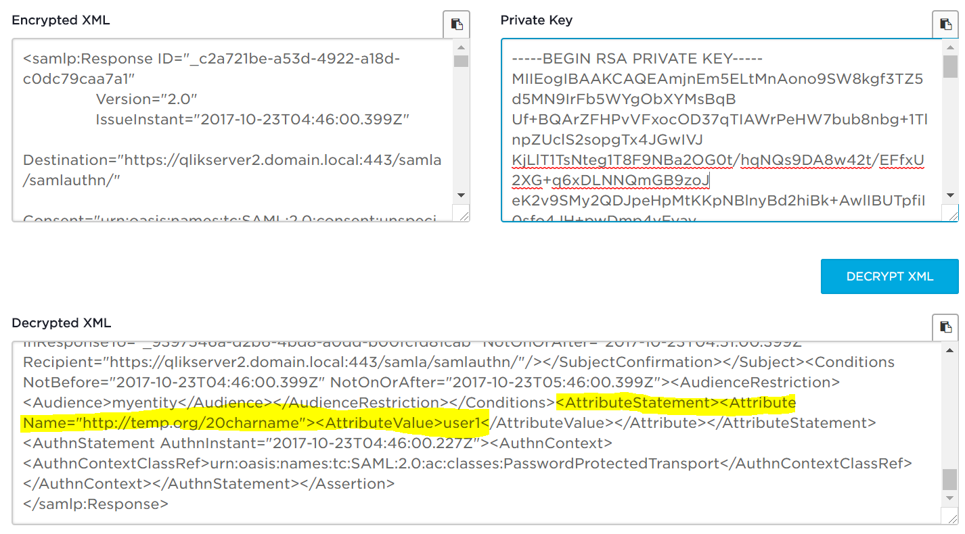
- Go to https://www.samltool.com/decrypt.php
- In Encrypted XML, paste the deflated/decoded SAML response.
- In Private Key*, paste the private key of Qlik Sense.
| * It must be the private key in clear text, not protected by a passphrase. A protected private key will begin with -----BEGIN ENCRYPTED PRIVATE KEY----- while a clear text private key will begin with -----BEGIN RSA PRIVATE KEY----- In order to decrypt a private key, you can use the command: openssl rsa –in enc.key -out dec.key You will be asked to enter the passphrase for your private key. Please note that openssl must be installed and you should run this command from the command prompt in the folder where the binary for openssl is installed. |
Related Content:
Qlik Sense Enterprise on Windows

Qlik Sense Enterprise on Windows
8,607 Views