- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Qlik Sense SAML Cryptography Errors with CryptographicException in Proxy Trace Audit log
Jun 7, 2021 10:31:20 AM
Jul 17, 2017 6:25:26 PM
When setting up SAML with Qlik Sense, a 400 or 500 error appears. The setup for the QMC Virtual Proxy and 3rd Party Setup is correct.
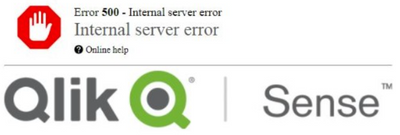
Error 500 - Internal server error
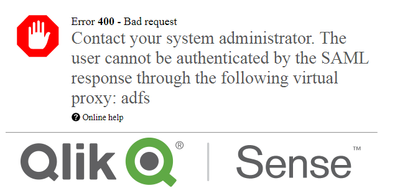
Error 400 - Bad Request
The Proxy Trace Audit log shows the following errors:
Unanticipated System.Security.Cryptography.CryptographicException occurred for connection
Environment:
Qlik Sense Enterprise on Windows
Resolution:
This suggests a need to change the Cryptographic Security Provider to use Microsoft Enhanced RSA and AES Cryptographic Provider.
Some relevant links for how to do this:
http://www.isolation.se/import-a-cryptographic-new-generation-cng-certificate-as-a-legacy-cert-to-us...
certutil.exe -csp "Microsoft Enhanced RSA and AES Cryptographic Provider" -importpfx c:\temp\cng_cerficiate_file.pfx
http://www.componentspace.com/Forums/1578/SHA256-and-Converting-the-Cryptographic-Provider-Type
SHA-256, SHA-384 and SHA-512 XML signatures require the Microsoft Enhanced RSA and AES Cryptographic Provider.
SHA-256 and Cryptographic Service Provider Types
This can be checked using Microsoft's CertUtil.
certutil -dump idp.pfx
Enter PFX password:
================ Certificate 0 ================
================ Begin Nesting Level 1 ================
Element 0:
Serial Number: 74f0ebfe22358db8433138f9558c9af9
Issuer: CN=www.idp.com
NotBefore: 22/11/2013 6:20 PM
NotAfter: 1/01/2050 12:00 AM
Subject: CN=www.idp.com
Signature matches Public Key
Root Certificate: Subject matches Issuer
Cert Hash(sha1): a6 a4 ae 4e 0b 37 8e c7 36 78 e5 81 26 90 af 50 e3 ec 37 69
---------------- End Nesting Level 1 ----------------
Provider = Microsoft Enhanced RSA and AES Cryptographic Provider
Encryption test passed
CertUtil: -dump command completed successfully.
The following command outputs information about the private key and certificate including the CSP.
openssl pkcs12 -in idp.pfx
Enter Import Password:
MAC verified OK
Bag Attributes
localKeyID: 01 00 00 00
Microsoft CSP Name: Microsoft Strong Cryptographic Provider
friendlyName: PvkTmp:b143944f-c289-4e3c-b9cc-37ce1e8ada19
Key Attributes
X509v3 Key Usage: 10
Enter Ctrl+C a couple of times to get back to the command prompt.
The Microsoft Strong Cryptographic Provider is suitable for SHA-1 XML signatures but doesn't support SHA-256 XML signatures.
The PFX can be recreated specifying the required CSP.
Firstly, it must be converted from PKCS12 to PEM format.
set RANDFILE=.\openssl.rnd
openssl pkcs12 -in idp.pfx -out idp.pem
Enter Import Password:
MAC verified OK
Enter PEM pass phrase:
Verifying - Enter PEM pass phrase:
Then it must be converted back to PKCS12 specifying the Microsoft Enhanced RSA and AES Cryptographic Provider.
openssl pkcs12 -export -in idp.pem -out new-idp.pfx -CSP "Microsoft Enhanced RSA and AES Cryptographic Provider"
Loading 'screen' into random state - done
Enter pass phrase for idp.pem:
Enter Export Password:
Verifying - Enter Export Password:
The new PFX file is now ready for generating SHA-256, SHA-384 and SHA-512 XML signatures.