- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
QlikView WebServer: Custom HTTP Header
Mar 20, 2024 11:26:18 AM
Jan 27, 2020 6:32:20 PM
The QlikView WebServer (QVWS) supports custom HTTP response headers as of release 12.30.
Custom response headers are defined in QVWS config.xml file.
Note that for QlikView deployments using IIS as a web server, custom HTTP headers must be configured in IIS.
An example use case for this is the introduction of HTTP headers preventing any possible ClickJacking vulnerabilities. This type of attack is mitigated by adding an X-Frame-Options HTTP response header, which can be used to indicate whether or not a browser should be allowed to render a page in a <frame>, <iframe> or <object>. Sites can use this to avoid clickjacking attacks, by ensuring that their content is not embedded into other sites. For more information on X-Frame-Options, see, for example, X-Frame-Options (Mozilla).
Environment:
QlikView (12.30 and later)
Resolution:
Configure Custom Headers
- Run text editor (e.g. Notepad) as Administrator
- Edit QlikView WebServer configurations file. Default path; C:\ProgramData\QlikTech\WebServer\config.xml
- Locate CustomHeaders element within the config file
- Replace empty element <CustomHeaders /> with open and closed elements <CustomHeaders></CustomHeaders> if needed.
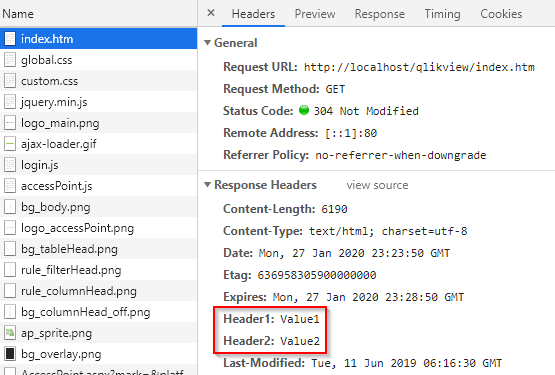
<Config> ... <Web> <CustomHeaders> ... </CustomHeaders> </Web> </Config> - Add custom response header as <Header> element(s) with sub-elements defining the desired header name and value.
<Config> ... <Web> ... <CustomHeaders> <Header> <Name>Header1</Name> <Value>Value1</Value> </Header> <Header> <Name>Header2</Name> <Value>Value2</Value> </Header> </CustomHeaders> </Web> </Config> - Restart QlikView WebServer service
Validate custom headers
- Open browser
- Enable browser developer tools
- Open QlikView AccessPoint
- Validate in HTTP response header that custom header has been set