Unlock a world of possibilities! Login now and discover the exclusive benefits awaiting you.
- Qlik Community
- :
- Support
- :
- Support
- :
- Knowledge
- :
- Support Articles
- :
- Qlik Sense Enterprise on Windows: Compatibility in...
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Qlik Sense Enterprise on Windows: Compatibility information for third-party SSL certificates to use with HUB/QMC
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Qlik Sense Enterprise on Windows: Compatibility information for third-party SSL certificates to use with HUB/QMC
Feb 21, 2023 7:18:39 AM
Apr 26, 2017 6:53:20 AM
A third-party certificate was configured in the Qlik Sense Proxy, but is not being used.
The connection is not private" NET::ERR_CERT_COMMON_NAME_INVALID may be displayed on HUB access.
Qlik Sense Enterprise on Windows uses self-signed and self-generated certificates to protect communication between services, as well as user web traffic to the hub and management console. It is possible to use a third-party-issued SSL certificate to protect client web traffic. Using the self-signed certificate will cause a certificate warning to be displayed in the web browser (such as Google Chrome or Internet Explorer).
If the third-party certificate for the Qlik Sense Proxy Service is not fully compatible with Qlik Sense or it does not have the correct attributes and cyphers, the Qlik Sense Repository Service will revert to using the default certificates. The following error may occur in the Proxy Security logs:
Example: C:\ProgramData\Qlik\Sense\Log\Proxy\Trace\HOSTNAME_Security_Proxy.txt
No private key found for certificate 'CN=qliksense.domain.com' ([CERTIFICATE THUMBPRINT HERE]) Couldn't find a valid ssl certificate with thumbprint [CERTIFICATE THUMBPRINT HERE] Reverting to default Qlik Sense SSLCertificate Set certificate 'CN=qliksenseserver1.domain.com' ([CERTIFICATE THUMBPRINT HERE]) as SSL certificate presented to browser
Resolution:
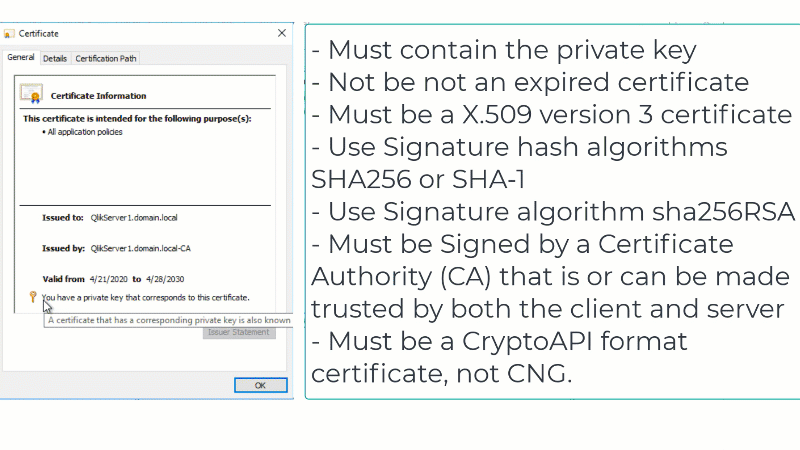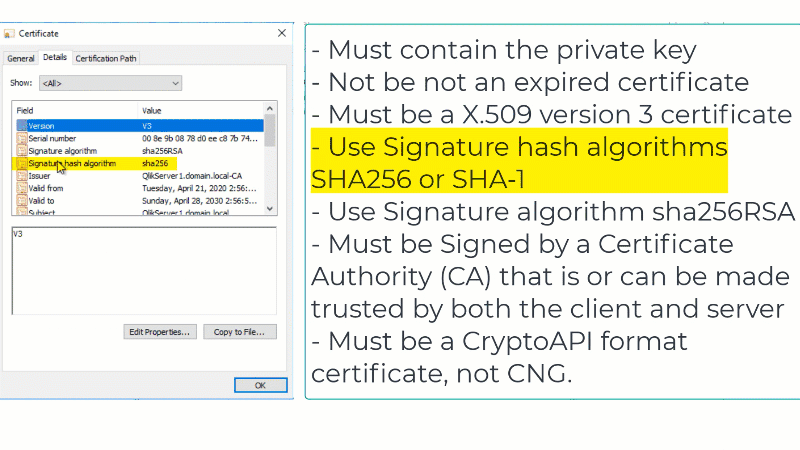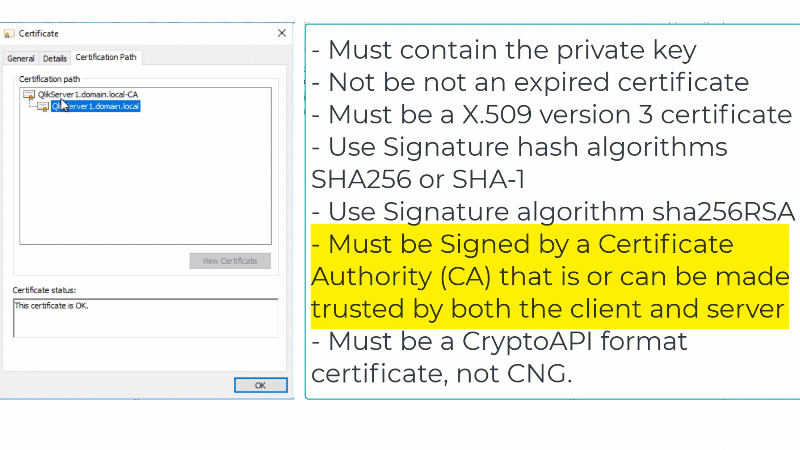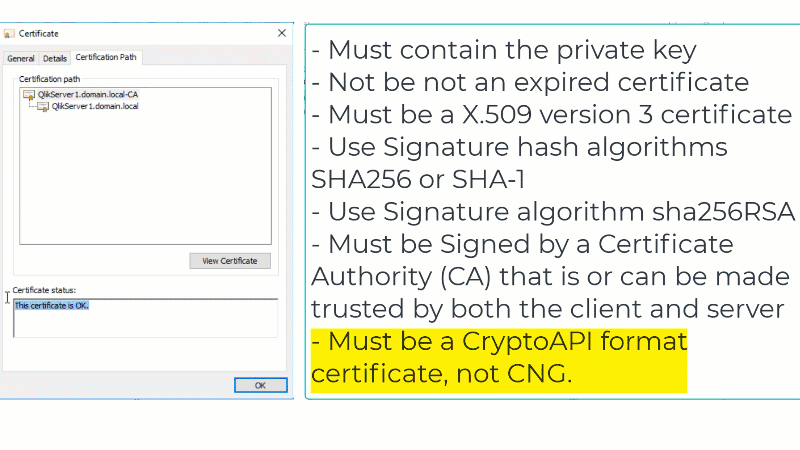
In order for Qlik Sense Enterprise to correctly recognize the third-party certificate as valid, the certificate will have to meet the following requirements:
Note: Root and Intermediate CA certificates need to be correctly installed. Should any be missing, Qlik Sense proxy will not use the server certificate and will revert back to using the self-signed certificate instead.
Certificates that are known to work well with Qlik Sense have the following attributes:
- Certificates that are x509 version 3. More information including filename extensions under https://en.wikipedia.org/wiki/X.509
- Use signature algorithm sha256RSA
- Use signature hash algorithm sha256
- Signed by a valid, and OS/browser configured , CA
- Are valid according to date restrictions (valid from/valid to)
- Key in format CryptoAPI (not in CNG)
- The certificate itself has to contain private key no matter what Qlik Sense version.
Related Content:
How to: Change the certificate used by the Qlik Sense Proxy to a custom third party certificate
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
@Andre_Sostizzo, @Sonja_Bauernfeind I wanted to check in and see if there are any updates to certificate attribute requirements. SHA1 hashing algorithm is not considered reliable anymore and CryptoAPI has been deprecated for more than two years now.
I'm assuming newer versions of Qlik Sense support more secure hashing algorithms and CNG providers but I can't find updated list of certificate requirements anywhere.
Would you be able to either provide a link to updated requirements or update this post that modern versions of Qlik Sense support?
Thanks,
Mikhail B.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Thanks for looking into this, Sonja! I appreciate it.
Also, a side note, the very last point in the list of requirements above states:
"The certificate itself has to contain private key no matter what Qlik Sense version."
Certificates, as far as I know, don't contain a private key. They contain a public key. More specifically, certificates contain a modulus and an exponent which are used to calculate a public key. Private key is securely stored on a server and never shared, unlike a certificate which is shared with every client PC requesting interaction with a server.
I believe that point should say:
"The server on which Qlik Sense is installed has to contain private key that is corresponding to public key contained within a certificate no matter what Qlik Sense version."
Mikhail B.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hello @mbespartochnyy
The private key statement does apply and refers to whether or not you import a certificate which has been exported to include a private key. See Requirements, or: What to look out for when getting your cert. and How to manage the Certificate Private Key. If a certificate is used which does not include this, the Qlik Sense Proxy will discard it and revert to the default self-signed certificate.
All the best,
Sonja
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Interesting. I've never heard of certificate containing a private key. Ever the message in the Certificate window in the GIF in this post and a screenshot in Requirements, or: What to look out for when getting your cert post that you've mentioned both says:
"You have a private key that corresponds to this certificate."
Public / private key pair is generated on a server and private key is stored in a secured key store on the server never to be shared with anyone including a CA. Public key along with server and organization information is included in a CSR and sent to a CA for verification and signing. CA, once verifies identity of a requester, then signs a certificate containing server's identity and public key and send the signed certificate back to the server. A server then uses this signed certificate to distribute it to client PCs. Client PCs validate CA signature from the certificate it receives from the server and, if validations is successful, client PC then use public key which is included in a certificate to securely exchange session keys. Server uses its securely saved private key to decrypt session keys and use the session keys to secure client / server communications from that point on.
It makes sense for client PCs to ignore certificates if a server doesn't have a corresponding private key because Qlik Sense server wouldn't be able to decrypt session keys it receives from client PC. Also a certificate is imported for which a server does not own a private key, that server wouldn't be able to use that certificate. I can't find anything on workings of PKI or TLS/SSL that suggest that private keys are ever contained within a certificate. Not to say that it's not possible. Do you have anything that you can share that would support the idea that private keys are included in certificates?
Mikhail B.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Just reread your message and noticed that you mentioned exporting of certificates. Certificates can be exported along with a private key. However export of certificate and private key is a step that someone would take during a backup process to ensure successful restoration of a Qlik Sense site rather than installing a newly received certificate from a CA.
Since the topic of this post is third-party certificates and the requirements of third-party certificates, I don't believe a statement like "[Third-party] certificate itself has to contain private key..." is accurate.
Mikhail B.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi @Sonja_Bauernfeind @mbespartochnyy I'm also facing issue "NET::ERR_CERT_COMMON_NAME_INVALID" . I tried all the ways, but still facing this error on developer tool. any suggestion. pls.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hello @balajibc64
Please post about your issue in detail in the Qlik NPrinting forum.
Include:
- The version of the product
- What you are attempting to do
- What steps you performed
- Where the steps fail and where you are seeing errors
Feel free to tag me in the post.
All the best,
Sonja